Month: November 2019
Virtual Inception – a dream inside of a machine inside of a machine
estudiante de la vida 0 Comments S.T.E.A.M.
If you do not have a Chief Technology Officer (CTO), investing in technology may not be a priority. To generate revenue, marketing and sales are treated as justified expenses, and technology is usually undervalued. However, if implemented correctly, technology will increase profit, through reducing costs and increasing productive output. As your technology connoisseur, one technology I recommend is virtualization. Whether you’re a small business owner or a residential user, virtualization has a lot of potential.
Continue reading “Virtual Inception – a dream inside of a machine inside of a machine”
Read MoreWhy United States end-users are so prone to cyber-attacks and what are our options!
estudiante de la vida 0 Comments S.T.E.A.M.
The cost of Networking
One of my favorite courses in grad school was advanced networking security. I enjoyed it so much, that it was the focus of my thesis. I remember asking my professor, “with our advanced networking security techniques and applications why are we so susceptible to cyber-attacks.” His response, “our archaic infrastructure”; “America doesn’t replace obsolete networks, we just add on and make things backwards compatible.” That was a Eureka moment, it’s cost effective to build on to an existing system, then to erase the system and start over. Thankfully, our scientists made great strides, so that we can have high speed internet access. They also figured out how to secure networks without sacrificing too much throughput. (speed at which the data travels)
However, we still have obsolete technologies (devices, protocols, systems, etc.) in place that compromise our most up-to-date systems. In my years of IT experience, I noticed the average end-user does not justify IT as a necessary expense. “Unlike marketing, something that earns revenue, if my systems are “working, why upgrade?” It’s unfortunate, but this is a thought shared by many. It isn’t until they are losing money before they act. By then it becomes an emergency and panic spreads. The pressure is now on your IT team to resolve the issue in a timely manner. IT teams can restore your computer after an attack and they can also attempt to deter the attacker. Unfortunately, there is nothing they can do to stop a relentless attacker. With all the money lost due to cyber-attacks, why have we not redone our infrastructures and use the latest technology in our homes and businesses? It still hasn’t become a justified expense. Unfortunately for us, other countries have decided IT is a necessary expense and invested in their infrastructure. I remember reading an article, some years back, that Korea had 10Gb LAN speeds already in existence, when we were rolling out 1Gb Lan speeds. If our advancement in technology can be interpreted as incremental snapshots; other countries use the most recent snapshot to build their infrastructures. This makes our competitors faster at exploiting our network vulnerabilities, leaving us with very little options. Continue reading “Why United States end-users are so prone to cyber-attacks and what are our options!”
Read MoreSecure your systems by arming yourself with knowledge
estudiante de la vida 0 Comments S.T.E.A.M.
 Network is where at least two nodes/hosts (laptops, desktops, mainframes, cellphones, …etc.) are communicating with each other. In a communication session, one host acts as a client (requesting information) and one acts as a server (providing information). When networks were first developed, a host either acted as a client or server at one time. Fortunately for us, scientists and engineers figured out how to improve communication by allowing devices to be both clients and servers simultaneously.
Network is where at least two nodes/hosts (laptops, desktops, mainframes, cellphones, …etc.) are communicating with each other. In a communication session, one host acts as a client (requesting information) and one acts as a server (providing information). When networks were first developed, a host either acted as a client or server at one time. Fortunately for us, scientists and engineers figured out how to improve communication by allowing devices to be both clients and servers simultaneously.
Types of Networks!
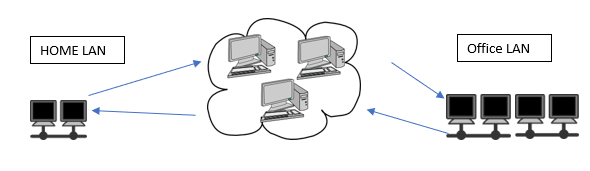
The internet is interconnection of networks. When you connect to the internet, the internet connects to you. There are two types of networks that makes up most the internet, Local Area Networks(LANS) and Wide Area Networks(WANS). The size of a network, i.e. the number of hosts in the network, doesn’t determine if it’s a LAN or WAN. It’s how the hosts connect and their geographic location that makes that determination. Most end users connect to a LAN, and LANs connect to each other through WANs. For example, when a small business owner downloads a file from their server, they have successfully connected to the office LAN. When the owner is home, and on their network-enabled printer, prints a file from a USB flash drive on their laptop; they were connected to their home LAN. Lastly, if the owner needed a file on the office’s network share, quickly and securely; they would log in to their company’s network via a VPN connection and retrieve the file. Because these two areas are most likely separate in geographic location; the owner needs to rely on their ISP(s) for a WAN connection.
Continue reading “Secure your systems by arming yourself with knowledge”
Read More