Category: S.T.E.A.M.
Content related to Science, Technology, Engineering, Arts and Mathematics.
Happy Birthday Grandma
estudiante de la vida 0 Comments My Life S.T.E.A.M.

Wow time is flying, it’s been two years since you left
But I know your energy is still with me, so I can’t really call it death
Although I really miss you and would give anything to have you near
I’m glad you’re with your creator, celebrating your 98th year.
Having fun with your husband, please send poppy my love.
Aunty Linda too, and everyone else above.
I want to see you all, so I’ll do my best on earth
For an entrance into heaven, I’ll definitely prove my worth
I so very often wish, I could call you like I’d do
Listen to your voice, while sharing a story with you
I’d get to hear you laugh, which definitely made my day
My bright and energetic sunshine, that broke through clouds so grey.
Well grandma, although you’re gone, I still can’t help to write you.
Hopefully heaven has email, and the angels will pass this message through.
I feel your energy surging, giving me strength to continue fighting
I’m sure you know how much you’re loved, probably could tell from this writing.
Happy Birthday Gorgeous!!!!
Read More
No Longer Here
estudiante de la vida 0 Comments S.T.E.A.M.
They try so hard, but will they ever de-soul me?
Got so many demons, like spectrum they try to control me
they put a ceiling over me, just right before I soar G
like a tire with a puncture, I get to my destination far too slowly
Persevering is so hard, but giving up is so easy
“hang in there kiddo", come on, that so cheesy
If I don’t believe in my self, How I can I expect some to believe me
I wanna ask for help, but will I appear weakly
I keep on running, but then I hit my wall
now barely out of breath, and I know I’m gonna fall
I begin and start to question, what was the purpose of it all
Then from the deep within, I hear a voice a call
I know you probably think that nobody is there
but this you have to know, I’ll always will be here
When you cry, I do cry, so please no more tears
My dark and clouded vision, suddenly becomes clear
I remember my purpose, I remember why I’m here
It’s not solely about me , it’s about the ones I hold dear.
Both the ones who love me in this world and the ones who are no longer here.
This Omnipotent voice, that helped me over the wall
was a combination of the people who saw me through it all
A sparkle in my eye, I stumble on a fact
So that’s the voice of God, yea I can get used to that.
I’m Trying to be the Best I can
estudiante de la vida 0 Comments S.T.E.A.M.
Alot of these rappers, yeah they ain’t saying nothin/
I’m really trying to hear them, So I switched to Verizon/
They new to the game, So I’m callingem my sons/
I claimem on my taxes, time for that refund/
Alot of dem wouldn’t last in my shoes/
They think this is a game but they don’t have a clue/
My moves already planned like I’m playing chess/
Studied holy books so I’m passing all his tests/
Continue reading “I’m Trying to be the Best I can”
Read MoreLEGO Mindstorms EV3 Robotics Lab 2
estudiante de la vida 0 Comments S.T.E.A.M.
LEGO Mindstorms EV3 Robotics Lab 2
LEGO Mindstorms EV3 Robotics
estudiante de la vida 0 Comments S.T.E.A.M.
Robotics Experiment 1
Just some experimenting with the robotics program to assist the students at my school
Virtual Inception – a dream inside of a machine inside of a machine
estudiante de la vida 0 Comments S.T.E.A.M.
If you do not have a Chief Technology Officer (CTO), investing in technology may not be a priority. To generate revenue, marketing and sales are treated as justified expenses, and technology is usually undervalued. However, if implemented correctly, technology will increase profit, through reducing costs and increasing productive output. As your technology connoisseur, one technology I recommend is virtualization. Whether you’re a small business owner or a residential user, virtualization has a lot of potential.
Continue reading “Virtual Inception – a dream inside of a machine inside of a machine”
Read MoreWhy United States end-users are so prone to cyber-attacks and what are our options!
estudiante de la vida 0 Comments S.T.E.A.M.
The cost of Networking
One of my favorite courses in grad school was advanced networking security. I enjoyed it so much, that it was the focus of my thesis. I remember asking my professor, “with our advanced networking security techniques and applications why are we so susceptible to cyber-attacks.” His response, “our archaic infrastructure”; “America doesn’t replace obsolete networks, we just add on and make things backwards compatible.” That was a Eureka moment, it’s cost effective to build on to an existing system, then to erase the system and start over. Thankfully, our scientists made great strides, so that we can have high speed internet access. They also figured out how to secure networks without sacrificing too much throughput. (speed at which the data travels)
However, we still have obsolete technologies (devices, protocols, systems, etc.) in place that compromise our most up-to-date systems. In my years of IT experience, I noticed the average end-user does not justify IT as a necessary expense. “Unlike marketing, something that earns revenue, if my systems are “working, why upgrade?” It’s unfortunate, but this is a thought shared by many. It isn’t until they are losing money before they act. By then it becomes an emergency and panic spreads. The pressure is now on your IT team to resolve the issue in a timely manner. IT teams can restore your computer after an attack and they can also attempt to deter the attacker. Unfortunately, there is nothing they can do to stop a relentless attacker. With all the money lost due to cyber-attacks, why have we not redone our infrastructures and use the latest technology in our homes and businesses? It still hasn’t become a justified expense. Unfortunately for us, other countries have decided IT is a necessary expense and invested in their infrastructure. I remember reading an article, some years back, that Korea had 10Gb LAN speeds already in existence, when we were rolling out 1Gb Lan speeds. If our advancement in technology can be interpreted as incremental snapshots; other countries use the most recent snapshot to build their infrastructures. This makes our competitors faster at exploiting our network vulnerabilities, leaving us with very little options. Continue reading “Why United States end-users are so prone to cyber-attacks and what are our options!”
Read MoreSecure your systems by arming yourself with knowledge
estudiante de la vida 0 Comments S.T.E.A.M.
 Network is where at least two nodes/hosts (laptops, desktops, mainframes, cellphones, …etc.) are communicating with each other. In a communication session, one host acts as a client (requesting information) and one acts as a server (providing information). When networks were first developed, a host either acted as a client or server at one time. Fortunately for us, scientists and engineers figured out how to improve communication by allowing devices to be both clients and servers simultaneously.
Network is where at least two nodes/hosts (laptops, desktops, mainframes, cellphones, …etc.) are communicating with each other. In a communication session, one host acts as a client (requesting information) and one acts as a server (providing information). When networks were first developed, a host either acted as a client or server at one time. Fortunately for us, scientists and engineers figured out how to improve communication by allowing devices to be both clients and servers simultaneously.
Types of Networks!
The internet is interconnection of networks. When you connect to the internet, the internet connects to you. There are two types of networks that makes up most the internet, Local Area Networks(LANS) and Wide Area Networks(WANS). The size of a network, i.e. the number of hosts in the network, doesn’t determine if it’s a LAN or WAN. It’s how the hosts connect and their geographic location that makes that determination. Most end users connect to a LAN, and LANs connect to each other through WANs. For example, when a small business owner downloads a file from their server, they have successfully connected to the office LAN. When the owner is home, and on their network-enabled printer, prints a file from a USB flash drive on their laptop; they were connected to their home LAN. Lastly, if the owner needed a file on the office’s network share, quickly and securely; they would log in to their company’s network via a VPN connection and retrieve the file. Because these two areas are most likely separate in geographic location; the owner needs to rely on their ISP(s) for a WAN connection.
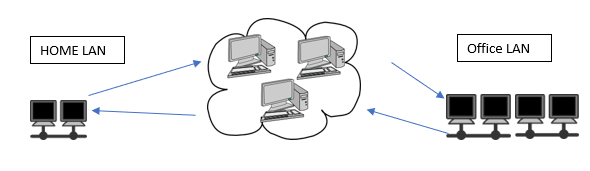
Continue reading “Secure your systems by arming yourself with knowledge”
Read More